Zillya! Total Security
The product with the highest level of protection!
Additionally, it has instrument of computer's control and module "Parental control".
This product is ideal for whose, who cares about information security of all family.
 Firewall
Firewall

Firewall
Sets the rules of incoming and outgoing connections for programs installed on your PC Anti-phishing
Anti-phishing

Anti-phishing
Blocks websites designed to steal personal user data Anti-spam
Anti-spam

Anti-spam
Blocks penetration of spam messages on the user's PC Parental control
Parental control

Parental control
Provides parents an effective tool for monitoring of child's activity on the PC Optimizer PC
Optimizer PC

Optimizer PC
Allows to identify junk system files and to free more disk space Process Manager
Process Manager
Process Manager
Allows you to control and manage running applications and processes. Startup Manager
Startup Manager

Startup Manager
Utility of workload optimization has been designed to increase the speed of your PC. Privacy protection
Privacy protection

Privacy protection
Program that allows to remove traces of the user's work on PC. Operative support 24/7
Operative support 24/7

Operative support 24/7
Round-the-clock telephone support for users.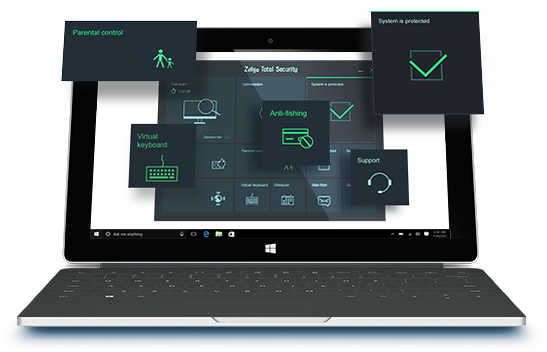
About product
Antivirus protects your PC from viruses, spyware, Trojans and other malicious programs.
The basis of data protection against all types of malicious software is built on the use of the actual virus database, containing over 15 million malware's signatures and advanced module of proactive protection.
This module is the core of the entire security system, which is based on the basis of Zillya! Total Security product. A unique feature of this module is modern virus signature database that is updated every day. It should be noted that such data do not overload neither server nor local PC, as the database is optimized and modernized. Thus, work with it does not affect the computer's performance and does not lead to hanging or slowing down of PC.
It is performed by means of a powerful firewall and WEB-filter, capable of up-to-date data check that come on the user's PC and to block sites with detected threats.
The presence of a firewall in the modern version of antivirus is a critical necessity. This module allows to significantly reduce the possibility of infection by malware via the Internet surfing. In addition, the firewall blocks the actions of malware that might get on the PC as unauthorized attempt to upload information from the Internet, reception of additional malicious components, new fraudulent or spyware capabilities.
The module allows to create your own "black lists" of undesirable Internet resources containing dubious or frankly objectionable materials. Web filter can also be used as an important part of anti-phishing security system based on databases of known spyware sites or suspicious sites that could potentially be involved in fraudulent activity.
Utilities will not overload your PC, because anti-virus consumes no more than 512 MB of PC's RAM.
It should be noted that such level of consumption is acceptable not only for modern personal computers, but also for those, which were manufactured 3-5 years ago. During Zillya! Total Security work, it does not block nor slow down the most unpretentious computers
The main rule of Zillya! is "Anti-virus protection is, above all, high-quality service".
The basis of a successful tech support is in-depth knowledge of the products, the desire to "listen" to user, to present information on the level at which it is clear to them. The secret of success is in the desire, the ability will also come.
The desire to understand the user and to help him or her is one of the tenets of the successful technical support. Recommendations of highly qualified specialist, described by "cool" slang, may be "empty words" for the client. While the help provided in simple terms, are a recipe for the solution of user's problems and the key to professionalism in the eyes of the user.
Optimizer is a tool that speeds up your PC. The software module allows to find unnecessary files and programs that overload operating system, and to remove them.The principle of its work is based on check of certain computer memory locations where temporary files are stored. To such categories optimizer attributes browsers' cache, search history, which they store, OS updates, "service" files and so on.
After scanning, the tool displays a list of all files, which are offered to be removed, and - most importantly, - their size alone, and the total amount of memory that will be released. The decision about removal takes user directly.
Parental control - The module, which allows to control visits to websites of the young PC users that their parents find undesirable.
It is important to understand that the essence of the “Parental Control” is to create a safe informational space of the child. Modern programs of parental control are complex filters that prevent minors from visiting certain sites, the content of which, according to their parents, is undesirable for viewing.
Process manager - It acts as built-in controller of applications and processes, allowing you to control and manage running applications and processes.
Process manager gives user the information on current working applications and services and also data of resources consumption. Utility allows to forcibly terminate undesirable processes, if they hang down, or excessively use memory that could adversely affect the performance of the PC.
Startup Manager - Utility of workload optimization is a program that allows you to analyze the applications that are uploaded at startup and to optimize boot time by disabling applications and some system functions that are not used.
Utility of workload optimization has been designed to increase the speed of your PC.
“Startup Manager” allows you to search for programs and services of operating system that is not used by the user, but still automatically uploaded and consume computer resources, and to disable their automatic upload.
Privacy Protection - program is a program that allows to remove traces of the user's work on PC. Module searches configuration and temporary files that were created during the operation of the standard software packages, and to perform their clean-up.
File Shredder is a special program that allows to safely remove the most unwanted sensitive files without the possibility of their recovery.
The way of operation of programs-shredders is that the file that is planned to be removed, is subjected to multi wipe-off. In fact, it is filled with meaningless information garbage (random numbers, characters, symbols etc.), which completely distorts its contents, without the restoration possibility. After this, it is removed from the hard drive. Even if such file would ever be found by hackers and they would try to restore it, they would not receive any benefit from such actions.
Zillya! Internet Security performs all the functions of antivirus protection, and contains:
- System File Checker in real time, which is designed to detect viruses and other malicious programs that try to penetrate the PC;
- Mail-filter - Mail filter checks all incoming and outgoing email messages for malicious objects, thus avoiding possible threats of infiltration in the system by means of e-mail.
- The heuristic analyzer that identifies new viruses, the detection entries for which are absent in the antivirus database;
- Three types of scanning:
Fast. To check the critical areas of the system;
Full. To scan all existing files on the computer;
Selective. To scan files according to the user's desire.
- Daily updates of antivirus databases for full protection of your PC.
- The automatic operative mode.
For users who do not have certain knowledge and skills to work with a firewall and its settings, has been implemented the automatic operative mode. In this mode, for applications that require for their work access to the network, automatically created rules that allow only outgoing traffic. This allows to optimally configure the security of the system, without any action from the user.
- Interactive mode is for experienced users.
In that case, if the user knows how to create firewall rules correctly, the product has an interactive mode. In this mode, user has 4 options:
Block all - completely blocks incoming and outgoing traffic for all applications;
Allow all - allows all incoming and outgoing traffic;
Allow only outgoing - allows the application to have only outgoing traffic;
Create a separate rule - allows to fully customize individual access parameters:
- to enable or disable a specific address (single address, range of addresses, the IP-addresses’ mask);
- to open or close specific ports (or to apply the rule to all ports for the application, to select the direction of traffic for these settings, to specify the protocol).
- Control of applications’ access to the network.
The firewall keeps track of all applications that attempt to access the network - both incoming and outgoing traffic;
- Protection against external attacks.
By default, the firewall allows applications only outgoing traffic. This allows to protect the system from attempts to access to it from the outside, since any incoming requests will be blocked.
- Built-in set of rules.
The program has a built-in database containing all the necessary rules to allow or to block (defined by the user) standard system services and protocols (NetBios, DHCP, DNS etc.) for work with the network. With their help, user can allow or block network activity on such protocols, leaving aside the intricacies of their work.
- The ability to set general settings for all applications in the system.
Zillya! Total Security is able to set general settings for all applications. For example, the user requires that all applications had access to a particular server. To do this, in the settings must be a rule that will allow access to a specific IP-address and to a specific port. And no longer will be necessary to create separate rules for access to this server for each application."
Products of new line have received innovative proactive technologies. One of the most important modules of all rage of antiviruses by Zillya! is the presence of so-called behavioral analyzer (HIPS).
This unique technology is the most advanced solution, which is implemented in the world's anti-virus industry. The essence of its work is scanning and analysis of programs, to determine likelihood of malicious behavior. If HIPS eoul notive that some program performs actions that could potentially harm your PC, it will be blocked even before its launch.
The new line of antiviruses by Zillya! has a function of self-defense.
It eliminates the possibility of disabling the protection of your PC as a result of the forced stop using the "Task Manager". This feature is implemented as a response to modern Trojans that are able to get administrative rights on the infected PC and block the work of installed programs, including non-modern antiviruses.
- Blocking of dangerous sites.
Zillya! Total Security has the ability to block access to potentially dangerous sites, stopping them from loading when viewed in a browser. In this case, the user sees a message;
- Block of potentially dangerous content from suspicious sites.
Some sites are added to the base of Zillya! Total Security as suspicious, or sites that have malicious content. If a site is in the list, you will be able to visit it, to view the pages, images, but you will not be able to download from this resource programs, files, documents and other files that may harm your computer.
- Create your own list of blocked sites.
In the WEB-filter, there is a possibility, in addition to the built-in database of blocked sites, to create your own list of sites that the user, for whatever reason, considers undesirable. To this personal base subjected the same rules that apply to the built-in base.
Security module of USB-drives controls the connection of any drive to the USB-ports. Preliminary analysis with following informing of user reliably protects the computer from automatically downloaded objects on disks. So now Zillya! will protect you from the automatic start from the flash drive of a virus or worm, even if it is a completely new, unknown virus.
When connecting a new USB-drive, Zillya! detects it, performs a brief analysis and informs the user about the evaluated level of security of the disc. In the case of detection of the viruses or any suspicious objects on the flash drive, antivirus immediately prompts the user to remove them.
Mail filter checks all incoming and outgoing email messages for malicious objects, thus avoiding possible threats of infiltration in the system by means of e-mail.
The modules are built on the principle of proactive technologies. They allow to set up a "black list" of e-mail addresses and websites that have been seen in spam mailings and phishing activity.
For example, Anti-Spam allows to make flexible adjustment of blocked messages. You can set the filter by sender, recipient, title, or subject. This will significantly reduce the probability of receiving unwanted emails.
Anti-Phishing allows to avoid sites that have phishing activity, steal user data and are used by cybercriminals for illegal enrichment.
The module, which allows to control visits to websites of the young PC users that their parents find undesirable.
It is important to understand that the essence of the “Parental Control” is to create a safe informational space of the child. Modern programs of parental control are complex filters that prevent minors from visiting certain sites, the content of which, according to their parents, is undesirable for viewing.
These resources include the following sites, related to:
- Social networks;
- Pornography;
- Games and Chats;
- Violence and Alcohol;
- Dating sites;
- Torrents;
- Online shopping;
- Gambling.
Actions of parental control based on list of network resources, access to which is defined as prohibited.
Functions of “Parental Control” that Zillya! Total Security has, include predefined lists of thousands pornographic sites, over 2,000 online gambling sites and over 1,000 resources, where violence and alcohol content is placed.
In addition, this database can be changed and supplemented manually with administrative rights, allowing you to customize the functionality of the module to make it more flexible and to take into account all the necessary requirements.
It acts as built-in controller of applications and processes, allowing you to control and manage running applications and processes.
Process manager gives user the information on current working applications and services and also data of resources consumption. Utility allows to forcibly terminate undesirable processes, if they hang down, or excessively use memory that could adversely affect the performance of the PC.
Process manager can regulate the work of:
• Applications,
• Processes.
Utility of workload optimization is a program that allows you to analyze the applications that are uploaded at startup and to optimize boot time by disabling applications and some system functions that are not used.
Utility of workload optimization has been designed to increase the speed of your PC.
“Startup Manager” allows you to search for programs and services of operating system that is not used by the user, but still automatically uploaded and consume computer resources, and to disable their automatic upload.
Privacy protection program is a program that allows to remove traces of the user's work on PC.
Module searches configuration and temporary files that were created during the operation of the standard software packages, and to perform their clean-up. This module allows to delete the following data:
- Lists of documents, opened by user;
- Temporary files;
- Saved passwords;
- List of popular programs;
- History of a browser.
Optimizer is a tool that speeds up your PC. The software module allows to find unnecessary files and programs that overload operating system, and to remove them.
The principle of its work is based on check of certain computer memory locations where temporary files are stored. To such categories optimizer attributes browsers' cache, search history, which they store, OS updates, "service" files and so on.
After scanning, the tool displays a list of all files, which are offered to be removed, and - most importantly, - their size alone, and the total amount of memory that will be released. The decision about removal takes user directly.
It is a special program that allows to safely remove the most unwanted sensitive files without the possibility of their recovery.
The way of operation of programs-shredders is that the file that is planned to be removed, is subjected to multi wipe-off. In fact, it is filled with meaningless information garbage (random numbers, characters, symbols etc.), which completely distorts its contents, without the restoration possibility. After this, it is removed from the hard drive. Even if such file would ever be found by hackers and they would try to restore it, they would not receive any benefit from such actions.
Minimum system requirements of Zillya! Total Security:
- Processor Speed – 1 GHz and higher;
- RAM – 1GB and more;
- Hard disk space – 1500 MB;
- Operating System – Windows XP (SP3), Windows 7 (х32, х64) (+SP1), Windows 8, 8.1 (x32, x64), Windows 10 (x32, x64), Windows 11 (x32, x64);
- Screen resolution – 1024 x 768 or higher (for the correct display of texts in the antivirus, the font size should not exceed 100% (the parameter is specified in the operating system settings in the display settings section).
* One PC means one operating system (OS)
Program Version: 3.0.2377.0

